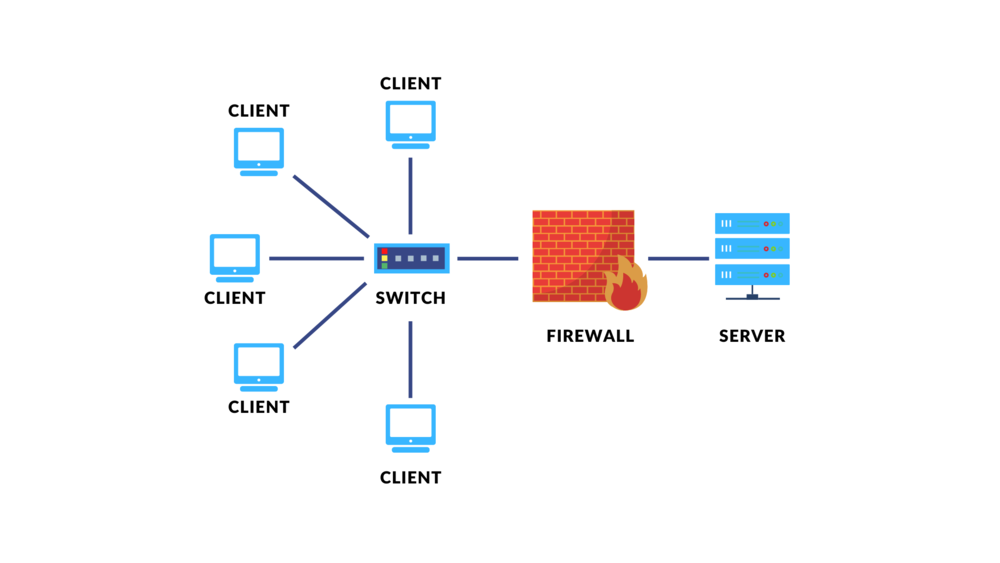
What is a Firewall?
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and untrusted external networks, such as the internet, to prevent unauthorized access and potential threats.
Functions of a Firewall
-
Access Control:
-
A firewall regulates access to and from your network by restricting which connections are allowed based on rules you set.
-
Traffic Filtering:
-
It filters network traffic to block suspicious or malicious data while allowing legitimate data to pass through.
-
Threat Detection and Prevention:
-
Firewalls can detect and prevent attacks such as malware, hacking, and other intrusions by blocking suspicious activities.
-
Logging and Monitoring:
-
Firewalls log network activities, which can be used to monitor and analyze attempts of attacks or security breaches.
Types of Firewalls
-
Packet-Filtering Firewalls:
-
These firewalls inspect packets (units of data) individually and make decisions based on a set of rules related to IP addresses, protocol, ports, etc.
-
Stateful Inspection Firewalls:
-
They keep track of the state of active connections and make decisions based on the state and context of the traffic.
-
Proxy Firewalls:
-
These firewalls act as an intermediary between users and the internet, inspecting incoming and outgoing data at the application layer.
-
Next-Generation Firewalls (NGFW):
-
NGFWs combine traditional firewall features with additional functionalities such as deep packet inspection, intrusion prevention systems (IPS), and application awareness.
How a Firewall Works
-
Rule-Based Filtering:
-
Firewalls operate based on a set of rules defined by the administrator. These rules specify which types of traffic are allowed or denied.
-
Traffic Monitoring:
-
All incoming and outgoing traffic is monitored and analyzed to ensure it complies with the security policies.
-
Action on Detection:
-
If the firewall detects any suspicious or unauthorized activity, it can take actions such as blocking the traffic, alerting the administrator, or logging the incident.
Example Implementation
Consider you are setting up a firewall on a Linux server using iptables, a popular firewall utility.
-
Installing
iptables:
-
Basic Configuration:
-
Allow all outgoing traffic:
sudo iptables -A OUTPUT -j ACCEPT -
Allow incoming traffic on port 22 (SSH):
sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT -
Block all other incoming traffic:
sudo iptables -A INPUT -j DROP
-
Saving Rules:
how to use firewall in proxmox:
proxmox have so many firewall interface what does that means?.okay if you see inside the dashboard like datacenter your node,or your vm theres firewal interface why proxmox have so much firewall interface?.every firewall have their own usage, firewall in data center thats mean you apply firewal to every u node and every vm you have so you dont need to setting it one by one.Firewall in node the usage is apply firewall to all vm inside the node or running from the node, and the last one firewall from the vm is for vm it self.if u wanna create/setting firewall you caThe “reject” action on a firewall is the process where the firewall not only discards unwanted packets but also sends a response to the sender to inform them that the packet has been rejected. n click firewall interface then click add,after you click add u must turn it on first by click option,firewall,edit,enable:yes
here examples of firewall implementation in proxmox :
direction: in(inside or data that enter) out(outside or data that sent outdside)
action:(action that will do in this firewall) ACCEPT (accept the data that send inside) DROP (action in a firewall refers to the practice of silently discarding network packets that meet certain criteria, without notifying the sender that the packets were discarded) REJECT (The “reject” action on a firewall is the process where the firewall not only discards unwanted packets but also sends a response to the sender to inform them that the packet has been rejected. )
source
interface: thats mean the bridge did you use the default bridge of proxmox is (vmbr0)
source:is where u put ur ip addres for spesific firewall setting
destination: is interface that will consider when determinig package is allowed or blocked by firewall
source ports:
refer to the port numbers used by the source of network traffic. When creating firewall rules, specifying source ports helps to control and filter network traffic based on the port numbers from which the traffic originates
Destination Port :
is the port number on the destination address that a data packet targets in a firewall rule. This port indicates a specific application or service on the destination side that you want to allow or restrict access to
macro interface:
is an abstraction layer that allows administrators to manage multiple network interfaces or configurations through a single interface. It often simplifies the management and configuration of complex network setups by grouping multiple interfaces into one logical entity.
example setting accpet all traffic that go into ur proxmox login or in:
-
Destination: in
-
acction:ACCEPT
-
interface:vmbr0
-
enable it
-
protocol: tcp
-
dst.port:8006
example setting allow one spessific ip use ping to ur server:
-
destination: in
-
Action: ACCEPT
-
enable it
-
source: (ip that u want to ping ur server) /32 (limits the scope to the one ip addres)
-
protocol: icmp
make device log in to ur server using ssh:
-
direction:in
-
action:accept
-
source:(ur ip)/32
-
dest.port:22
-
protocol: ssh
after configuration always turn on the firewall in the option